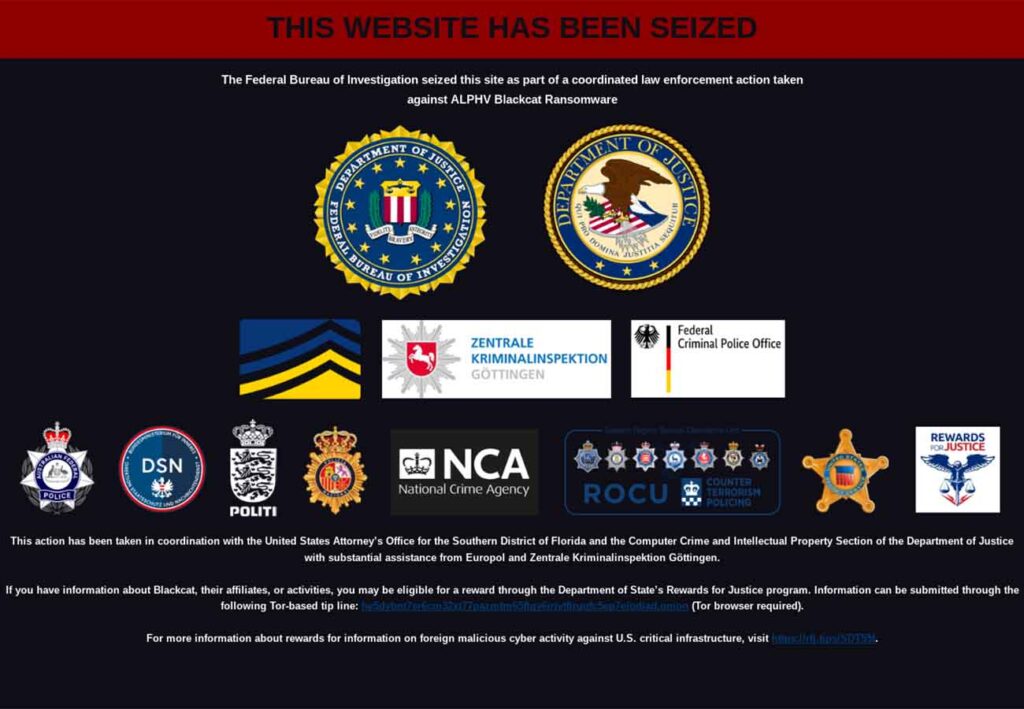
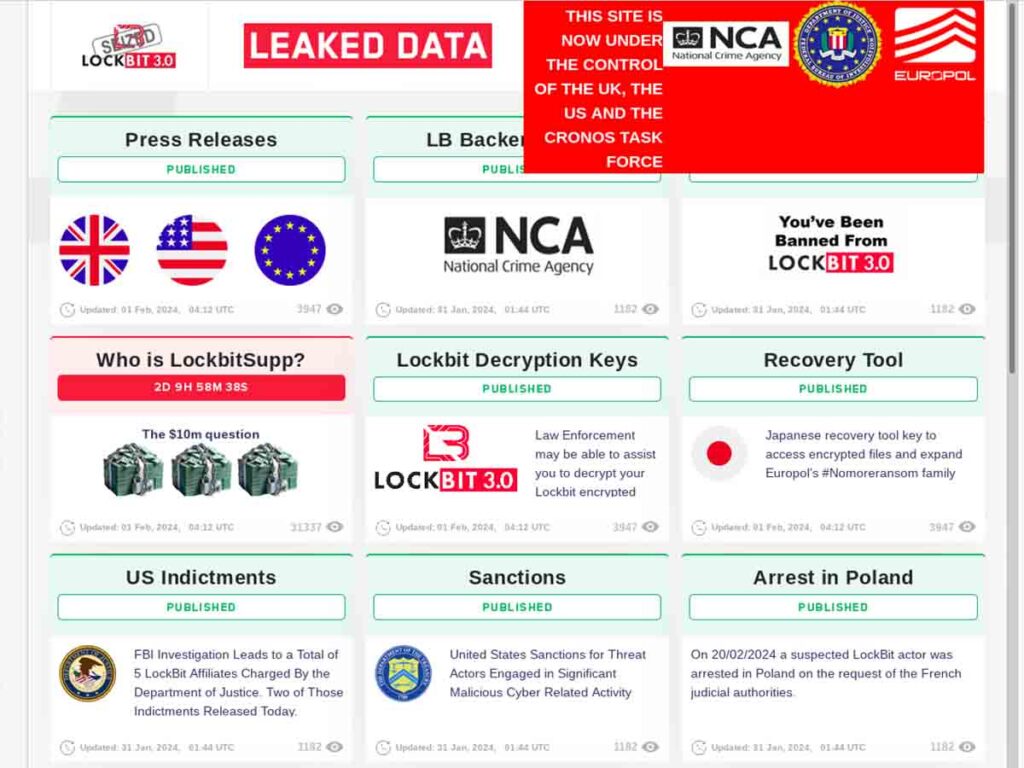
The Second Disruption of ALPHV/BlackCat Operations
The ALPHV/BlackCat infrastructure experienced its second shutdown since December 2023. Key Takeaways The affiliate alleged that the operator pocketed a $22 million ransom payment for […]
The Second Disruption of ALPHV/BlackCat Operations Read More »