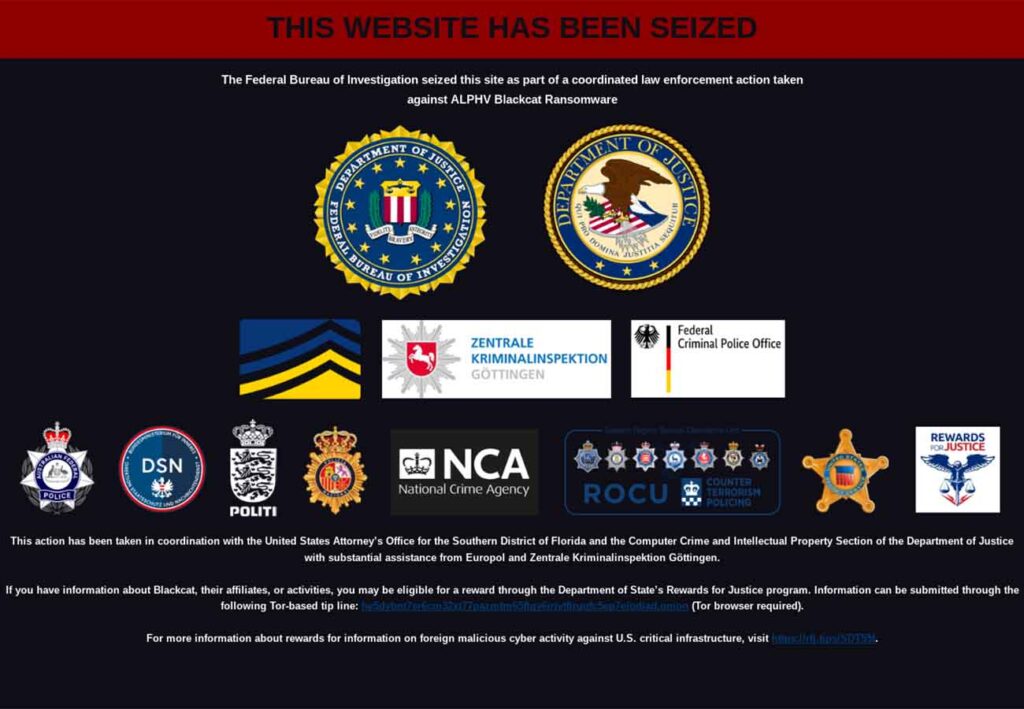
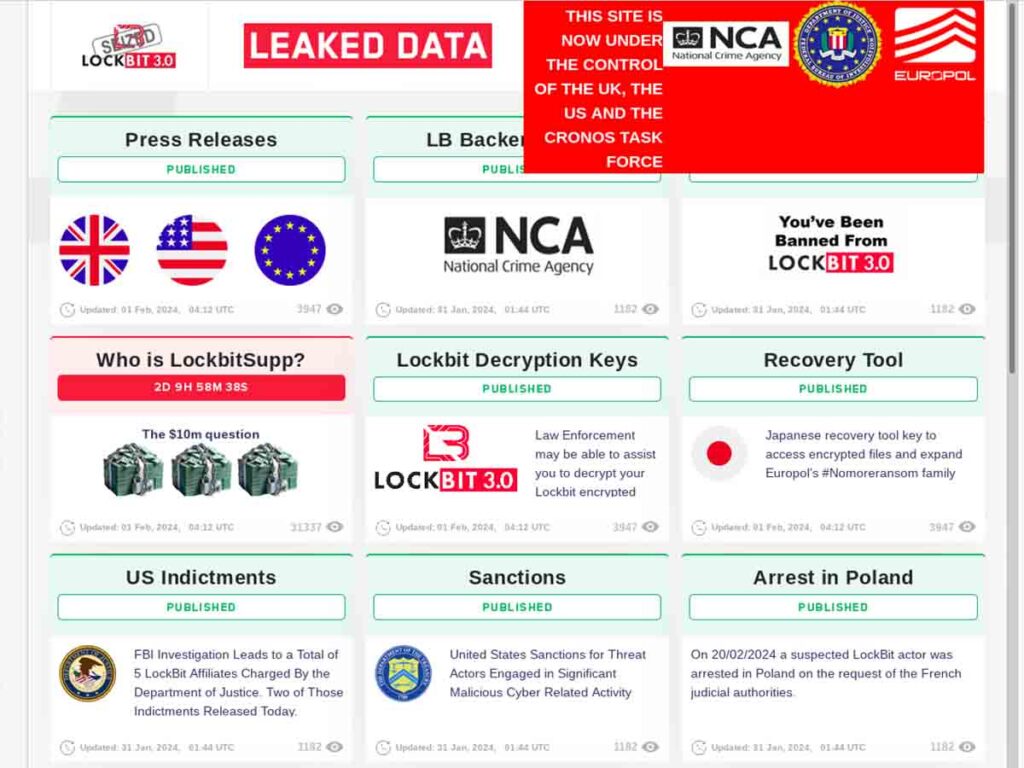
Expansion Bus Types, Speeds, and Their Implications for Cybersecurity
Expansion buses, both legacy and modern, serve as critical pathways for connecting devices like storage, GPUs, and peripherals to a computer’s motherboard. While modern buses […]
Expansion Bus Types, Speeds, and Their Implications for Cybersecurity Read More »